Aren’t phish great? Threes black phish, blue phish, old phish, new phish….. oh wait phish are no fun at all! Yet just like their much more interesting and worthwhile homophonic namesakes, there sure are a lot of them out in the deep waters of the world wide web. And just like the much more adorable fish, there are many different kinds of phish to be on the lookout for. This week we will be looking at the broad stroke categorization of different types of phishing scams that you may encounter out in the wild. It’s important to bear in mind that this list is not all inclusive simply because it cannot be. There are many malicious actors out there who make it their full-time job to come up with new ones so you must always be on alert. That said, the following are the most common phish encountered on any excursion into the water.
Varieties of Phish and their individual dispositions
- Email Phishing - Email phishing is the most common form of phishing. Attackers send deceptive emails, often impersonating trusted entities such as banks, companies, or government agencies. These emails typically contain urgent requests for personal information, login credentials, or financial details. Be cautious of unexpected emails, verify the sender's authenticity, and avoid clicking on suspicious links or downloading attachments.
- Spear Phishing – Unlike the broad ‘shotgun’ approach phishing typically employs, spear phishing is a targeted form of phishing that focuses on specific individuals or organizations. Attackers tailor their messages to appear more personalized, often using publicly available information or leveraging social engineering techniques. Spear phishing emails may reference personal details or colleagues to appear legitimate. Stay vigilant, question unexpected requests, and independently verify any suspicious communication.
- Smishing - Smishing, or SMS phishing, involves phishing attacks conducted through text messages. Attackers send deceptive texts containing links or prompts to respond with sensitive information. These messages may appear as urgent notifications or prize announcements. Exercise caution when receiving unsolicited texts, avoid clicking on links, and verify the authenticity of any requests.
- Vishing - Vishing, or voice phishing, occurs when attackers make phone calls posing as legitimate entities, such as banks or tech support. They attempt to deceive victims into revealing sensitive information or providing access to their devices. Remember that most organizations will never request your password over the phone. Be skeptical of unsolicited calls and avoid sharing personal or financial details.
- Pharming - Pharming involves redirecting users to fraudulent websites without their knowledge. Attackers manipulate DNS settings or exploit vulnerabilities to redirect users to malicious sites that mimic legitimate ones. These fake websites aim to collect personal information or install malware. Always verify the website's URL and be cautious of websites requesting sensitive information.
Ways of defending yourself from the predatory instincts of phish
- Develop a Security Mindset - Maintain a skeptical attitude towards unsolicited requests for personal information, even if they appear legitimate. Be cautious of urgency or threats designed to manipulate your emotions.
- Verify Sender Authenticity - Check email addresses, domain names, and phone numbers for any signs of manipulation or inconsistencies. Legitimate organizations often use official domain names and have established communication channels.
- Be Cautious of Clicking - Avoid clicking on links or downloading attachments from unsolicited emails, texts, or websites. Hover over links to check their destination URLs, and manually enter sensitive website addresses when in doubt.
Beware of the signs of an impending Phish attack!
- Urgent call to action or threats – Often times this will come in the form of a threat of criminal prosecution or a financial penalty if the action the sender wants is not taken immediately.
- First time senders – While it is not unusual to receive emails from new individuals, one should take an extra moment to scrutinize any communication from an unknown sender.
- Spelling and grammar mistakes – Emails from professional organizations are often scrutinized before being published, so a high number of spelling and grammar mistakes are often a sign of being an awkward translation, or an intentional effort to evade spam filters.
- Generic greetings – organizations that work with you most often will personalize their communications to you, rather than relying on generic greetings such as “Dear sir or madam”.
- Mismatched email domain – Be mindful of the email address from any new email you receive. For example, if you receive an email claiming to be from your bank, but you see that the email address it was sent from ends with ‘@gmail.com’, you can be reasonably confident that the email is not from your bank.
- Suspicious Links and attachments- never open links or attachments from any email that you have suspicions about, or do not know where they are coming from.
I caught a Phish, yuck! What do I do with it?
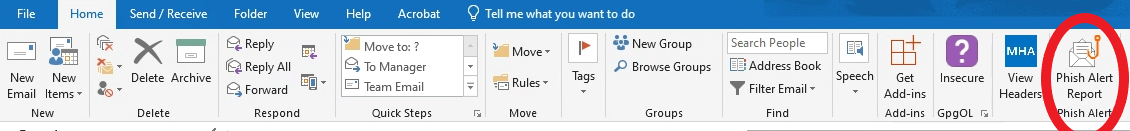
If you are on the desktop version of outlook, simply click the “Phish Alert Report” button on the upper right hand of the screen.
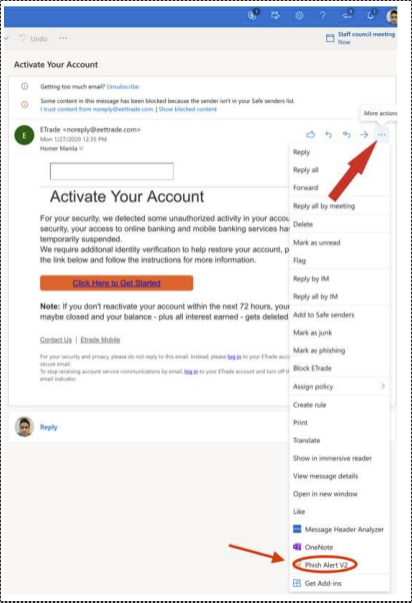
If you are on Outlook Web Access (Outlook on your internet browser), look for the three dots (ellipsis) on the open email, right next to the reply and forward arrows, and click onto the drop down menu to find the Phish Alert V2 option.
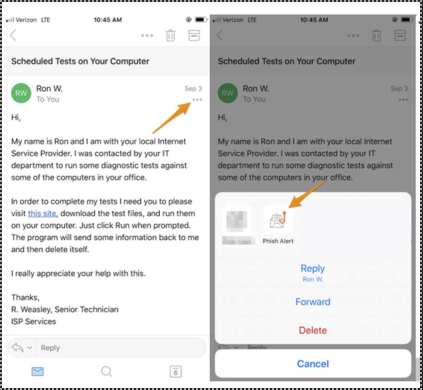
If you are on the Outlook Mobile App for iOS(this one can be slightly confusing), look for the ellipsis not at the top right of the screen, but on the top right of the open email just below the date. Tap on it and a menu with the Phish Alert option will appear.
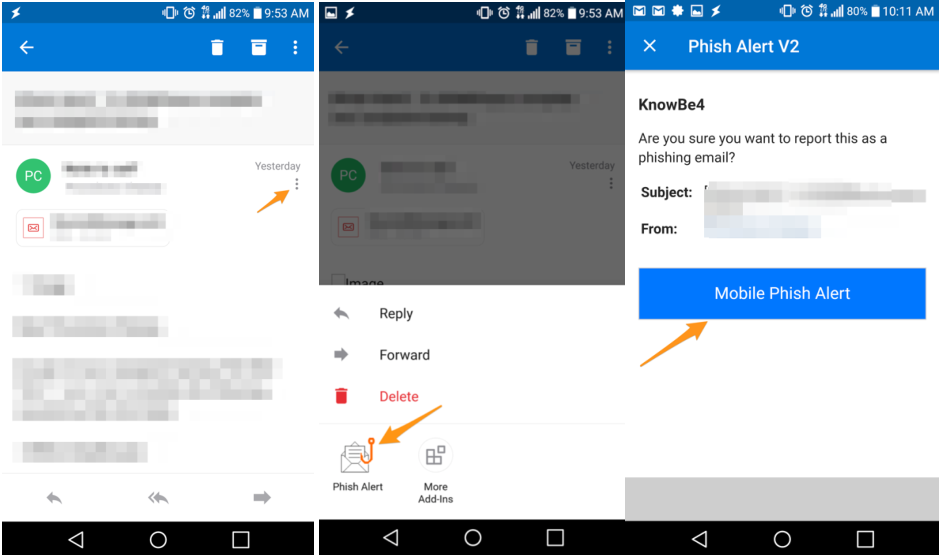
If you are on the Outlook Mobile App for Android(this one can also be confusing), look for the ellipsis not at the top right of the screen, but on the top right of the open email just below the date. Tap on it and a menu with the Phish Alert will appear.
For more information, please refer to this training document.
Thank you for staying vigilant!
--WU ITS Information Security