Virtually everyone has some kind of presence on social media, be it sharing pictures with friends on Instagram, writing posts on Facebook walls, or even lurking on Reddit. It is a nearly unlimited source of many kinds of varied content to both learn from and be entertained by, but it is also a hunting ground for the more nefariously minded. With some clever presentation, data manipulation, and careful targeting, you could find yourself out of control of your digital identity, and in doing so, potentially bring danger to yourself as well as your friends and family. The real-life example we wish to bring to your attention this week was found on Instagram.
Sharing an interesting photo on Instagram; what could happen?
It’s the spring of 2020, the sun is finally starting to come out and the world is turning from the drab monotony of winter, the birds are out, and the warmth is waking up the world. And you are feeling pumped! You contact some friends on Snapchat and decide let’s go hang out at the lake; it’s been too long and you’re dying to spend some time outside finally. You hurriedly put on your favorite North Face jacket, a gift from last Christmas, and enjoy a solid afternoon with your friends catching up and enjoying being all together again outdoors. To commemorate the event, everyone gathers around, and you get an amazing picture of everyone together, and you post it up on Instagram for all your other friends and family to see and perhaps get some measure of the enjoyment you now feel. Not long after, however, you receive an Instagram message that gives you a start. North Face is informing you that you had unwittingly committed copyright infringement and if you do not clear it up, your entire account will face deletion within 24 hours! Not wanting to lose your connection with all these people nor the pictures therein, and wanting to clear things up with your favorite clothing brand, you click on the link so thoughtfully provided and log in with your Instagram account and fill out some other pieces of information: address, phone, and email. You quickly receive a reply that comfortingly tells you that the matter is now resolved. And that is how they get you.
This sequence of events is similar to what happened to an unknown number of well-meaning victims in 2020, and was reported on by Andy Day with FStoppers. The scam message sent out to thousands of came from an account with over 150,000 followers ‘North Face Chile’, either set up by the scammers themselves or they had somehow gained control of the legitimate one. Here is what the victims saw:
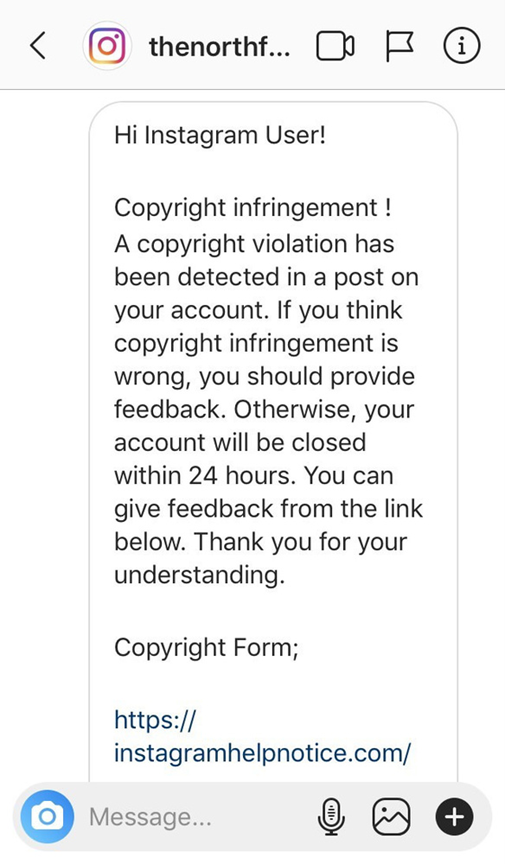
There are several things that will stand out to an alert observer, such as the nonspecific address as well as a lack of specificity as to what image is purportedly a copyright infringement. There are the classic hallmarks of poor grammar and punctuation, however this one is better than most. The biggest red flag is the website URL at the bottom of the message, as it leads outside of Instagram to a generic website. Word to the wise, if this was a link from Instagram itself, it would be hosted by an Instagram website URL. If you had clicked on the URL, you would have been brought to this page:
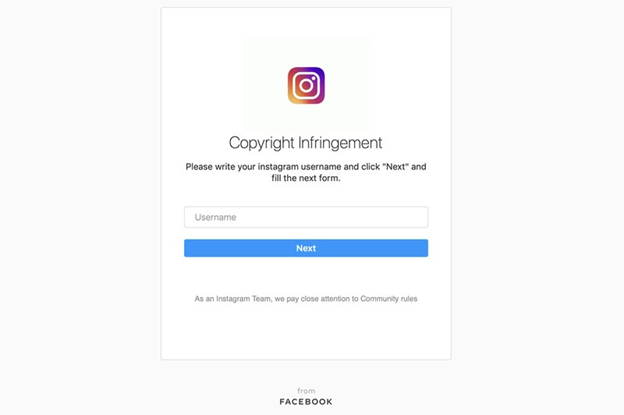
It almost looks just like an Instagram page doesn’t it? But, outside of the strange address, notice the bit of text under the Next button, “As an Instagram Team, we pay close attention to Community rules.” Sounds a bit off, doesn’t it? Any time you find examples of odd text coming from what is supposed to be a company(or especially a large corporation!), it bears investigation to make sure you are in fact communicating with the right people.
What are some ways of protecting myself?
As this example is a phish that was set loose on social media, the rules for both apply. On social media you should always:
- Strengthen Your Privacy Settings - Regularly review and adjust your privacy settings on social media platforms to control who can access your personal information and posts. Limit the visibility of your profile to people you know and trust.
- Exercise Skepticism - Maintain a healthy skepticism when interacting with unknown profiles or receiving unsolicited messages. Be cautious of requests for personal information, financial assistance, or requests to click on suspicious links. Verify the identity of the person through alternative means (don’t be afraid to call someone at a trusted/known number!) before sharing any sensitive information.
When you receive a strange message on social media, you should always be alert for:
- Urgent call to action or threats – Often times this will come in the form of a threat of criminal prosecution or a financial penalty if the action the sender wants is not taken immediately.
- First time senders – While it is not unusual to receive emails from new individuals, one should take an extra moment to scrutinize any communication from an unknown sender.
- Spelling and grammar mistakes – Emails from professional organizations are often scrutinized before being published, so a high number of spelling and grammar mistakes are often a sign of being an awkward translation, or an intentional effort to evade spam filters.
- Generic greetings – organizations that work with you most often will personalize their communications to you, rather than relying on generic greetings such as “Dear sir or madam”.
- Mismatched domain – Be mindful of the website address from any new message you receive. For example, if you receive a message claiming to be from the social media site, but you see that the link it is directing you to is outside of the social media site, you can be reasonably confident that the message is not from your social media platform.
- Suspicious Links and attachments- never open links or attachments from any email that you have suspicions about, or do not know where they are coming from.
Did you know October is National Cybersecurity Awareness Month? Watch this space or https://www.washburn.edu/cybersecurity all month for more security tips!
Thank you for staying vigilant!
--WU ITS Information Security
